App Configuration Management Settings
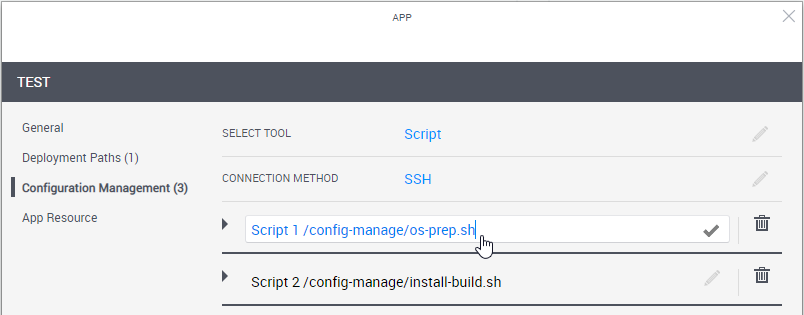
When adding or editing an App, click Configuration Management and configure the application to be installed on the VM
To learn how to develop custom scripts and Ansible playbooks, including examples, and set up support for the desired configuration management tool, see Developing Configuration Management Scripts for Apps.
-
To run configuration management on an Azure App, make sure the App's VM size is Basic_A2 or larger.
-
For configuration management operations, CloudShell uses an available Execution Server (for Ansible, it's a Linux Execution Server that has the Supports Ansible flag).
If the cloud provider resource has an Execution Server Selector configured, it will use that selector. If the selector is empty, CloudShell will use the selector defined in the appropriate Resource Manager Client >Configuration Services model (Ansible Configuration or Custom Script Configuration).
-
Execution Server selectors specified on the deployed App shell/resource are not used to execute configuration management operations.
- Define the script or playbook to install.
| Attribute | Description |
|---|---|
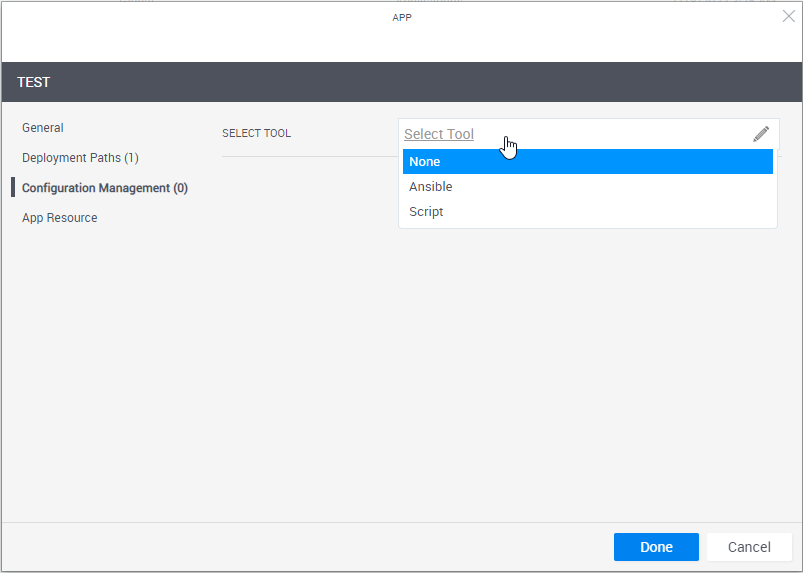
| Select Tool | Select the application's installation and configuration tool.
note The playbook runs once during the Setup phase for all of the sandbox's Apps that use that playbook, after CloudShell has finished deploying their VMs. This is done both to improve performance and support cross-server logic where multiple applications need to be installed and configured in a certain way. Depending on the selection, additional options may become available. |
| Connection Method | The method to use to connect to the VM. Select:
note To run configuration management on a Windows VM, the VM must have WinRM enabled. For details, see Enable WinRM on Windows VMs to Support Configuration Management. |
| Playbook / Script Location | Details of the Ansible playbook or custom script.
tip The URL can accept parameters defined on the App, enabling you to test new versions of scripts without affecting consumer-ready versions. For example, you can have an App everyone is using, but if you want to test a version you're developing, simply change the value of the URL parameter in the test blueprint.
For GitHub, specify the raw URL. For example: For GitLab, specify the API endpoint in the format: Where:
For BitBucket Data Center (on premise), use the following URL format: For BitBucket Cloud, use one of the following:
Important If the URL is private (HTTPS), the VM will need to have a valid SSL certificate. To disable the certificate check, open Resource Manager Client>Resource Families>Configuration Services (Ansible Configuration or Custom Script Configuration) and set the Verify Certificate attribute to False.
Notes
|
| Inventory Groups | (For Ansible) Specify the host groups for the application to be installed, separated by semicolons (;). The newly deployed VM will be associated to these groups, thus allowing plays that target these groups to run on the VM. For example: |
| Parameters | Parameters to be passed to the Ansible playbook or custom script. Specify the parameters and their default values. In the blueprint or sandbox diagram, privileged users can also set the parameter to receive the value that is specified for a global input when reserving a sandbox containing the App. This is done by selecting the global input when editing the App in the blueprint or sandbox diagram. For example, a global input that specifies the build number of a product to be tested or which components of a product to install. (For Ansible) To customize the port to be used to communicate with the VM, add the |
| Additional Arguments | (For Ansible) Define arguments to be passed to the execution of the playbook ( The arguments must be specified in Resource Manager Client > Configuration Services family > Ansible Configuration model > Ansible Additional Arguments attribute. Note: The arguments are defined globally for all Apps using Ansible. Important: To configure Ansible to connect to certified hosts only (Linux VMs with a valid 'known_hosts' key), include the following additional arguments: |
-
To enable the end-user to rerun the App's configuration management on the deployed App in the sandbox, select Allow rerunning configuration management for resources deployed from the App. Once the App's deployment completes, a Rerun Configuration Management command is included in the deployed App's Application Commands pane. For details, see Run App Commands. This is useful for rolling back the App's VM to its original state.
-
To enable blueprint and sandbox owners to modify the App's Configuration Management details, select Allow blueprint/sandbox owners to modify the App's Configuration Management. The following details can be modified: playbook/script, authentication details, inventory groups, and parameters. Note that the modifications only apply to the blueprint or sandbox of the instance.
-
Optionally click the Add New Script/Playbook link at the bottom right to add additional custom scripts/Ansible playbooks to the App. The scripts will run in their display order, from top to bottom. You can drag scripts up or down to rearrange.
-
To change the script's alias, click the script's name and change as appropriate.