Adding AWS EC2 Cloud Provider Resource
The use of an AWS EC2 cloud provider resource requires a Management VPC to be installed and configured on an AWS region. For additional information, see AWS Integration.
The AWS EC2 cloud provider enables the deployment of AWS instances from an Amazon Machine Image (AMI).
We strongly recommend using the 2nd Gen version of the shell, which provides significant enhancements and capabilities, and is tamper-resistant from within CloudShell, ensuring your Azure cloud provider resources and Apps are in pristine condition. Useful articles: Replacing the 1st Gen shell with a 2nd Gen version, Cloud Provider Shells - Features and Capabilities Per Release.
To add an AWS EC2 cloud provider resource:
-
Log in to CloudShell as administrator and access the required domain. This will enable the Apps based on this cloud provider resource to be usable in this domain. For additional information, see Managing Public Cloud Apps in Domains.
-
In the Inventory dashboard, in the Resources tab, click the folder in which you want to create the resource.
-
Click + Add New.
-
In the Create New Resource dialog box, select the AWS EC2 cloud provider template. To use the AWS 2nd Gen shell, select Amazon AWS Cloud Provider Shell 2G.
-
Enter a Name for the AWS EC2 resource.
noteThe resource's name has a limit of 100 characters and can only contain alpha-numeric characters, spaces, and the following characters: | . - _ ] [
Access to the AWS account is provided using the IAM role configured in the Management VPC.
-
Click Create.
The Resource dialog box is displayed.
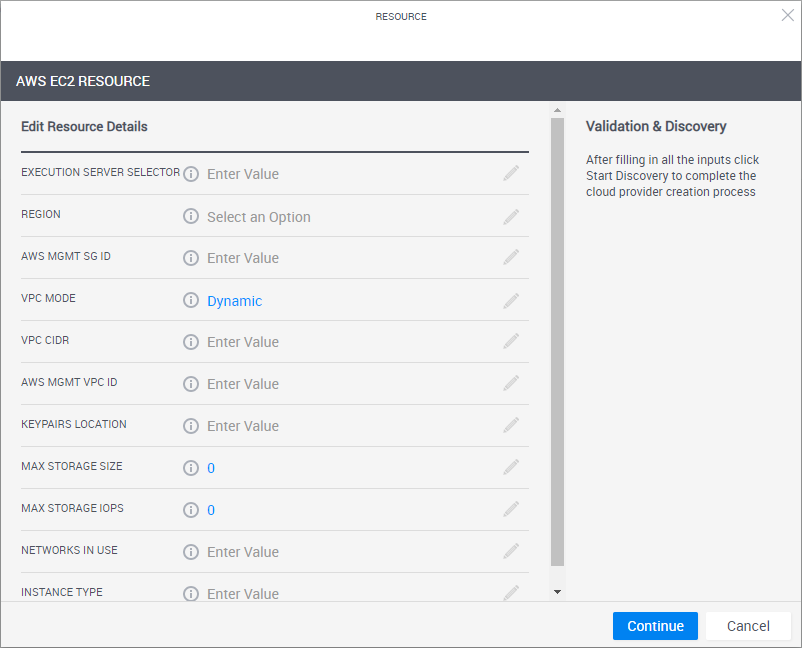
-
Enter the required information.
noteAll AWS elements must belong to the specified region.
Attribute Supporting shell version Description Region All The code of the AWS region to be used by this cloud provider resource. For example, "us-east-1".
noteThe AWS region must have Management VPC configured. For the list of supported regions, see AWS Regions Supported by CloudShell.
VPC CIDR AWS 1st Gen shell only CIDR to be used for sandbox VPC if VPC Mode is set to Static.
AWS Mgmt SG ID All The Management VPC's security group (use the SG1id output when configuring the Management VPC for the region). For example, "sg-71240198".
This value is used by the Setup process to configure the communication between the Management VPC's instances and the Sandbox instances.
AWS Mgmt VPC ID All ID of the Management VPC. Used by the Setup process to set up the VPC and subnet for the sandbox (use the ManagementVPCID output when configuring the Management VPC for the region). For example "vpc-633fb904".
This value is created when configuring the Management VPC for the region.
Keypairs Location All S3 bucket containing sandbox PEM files (use the S3Name output when configuring the Management VPC for the region).
Each active Sandbox creates a PEM file under a designated folder. For example, "sandbox-management".
Max Storage Size All (Optional) The maximum number of GiB in the root volume. The value of this parameter will be the storage size limit for all apps deployed on this Cloud Provider. For example, "8".
The value must be greater than or equal to the size of the root snapshot used. If set to "0", the default size of the snapshot will be used.
Max Storage IOPS All (Optional) The maximum number of I/O operations per second to be supported by the volume. The value of this parameter is the storage IOPS limit for all Apps deployed on this Cloud Provider. For example, "240".
This parameter is used only for storage of type io1, in which you can provision up to 30 IOPS per GiB. If set to zero, the default in the image is used.
Networks In Use All Reserved networks that will be excluded when allocating sandbox networks, and therefore must include the Management VPC CIDR (which was provided as an input to the CloudFormation deployment process) as well as any other private networks that have access to the Management VPC.
The syntax is comma separated CIDR. For example,
10.0.0.0/32,172.31.0.0/24.Instance Type All (Optional) The default AWS EC2 instance type for the deployed instance. The instance type determines the CPU, memory and networking capacity of the instance to be deployed. For example “t2.large”.
noteThe instance type can be changed when creating the App in the Manage dashboard.
Region All VPC Mode All Every sandbox with AWS Apps deploys a VPC to AWS, while in Shared VPC mode, CloudShell deploys the sandbox to an existing VPC. This setting determines how the sandbox VPC selects a CIDR block.
Options are:
- Dynamic: The CIDR block is selected by Cloudshell Server. In other words, CloudShell deploys a new VPC with a dedicated CIDR for every sandbox.
- Static: The CIDR block for all sandboxes allocated is taken from the VPC CIDR attribute. To configure CloudShell to support this mode, see the Typical Workflows of the AWS EC2 2G shell's README file.
- Shared: Indicates that the cloud provider resource will deploy to the shared VPC defined in Shared VPC ID and use the CIDR block defined in the VPC CIDR attribute.
- Single: The sandbox infrastructure will be deployed within the Management VPC and use the VPC CIDR block.
Static VPC CIDR AWS 2nd Gen shell only CIDR to be used for sandbox VPC if VPC Mode is set to Static.
Shared VPC ID AWS 2nd Gen shell only (Mandatory for Shared VPC mode) Shared VPC's ID (can be found in the output of the shared VPC CloudFormation stack, in the SharedVPCId key). For example:
vpc-0bf24b1ebrd855e30.Shared VPC Role ARN AWS 2nd Gen shell only (Mandatory for Shared VPC mode) Role created by the CloudFormation process with read/write permissions in the AWS account (can be found in the output of the shared VPC CloudFormation stack, in the SharedRoleARN key). This role is used by CloudShell to operate in the shared VPC.
Transit Gateway ID AWS 2nd Gen shell only (Mandatory for Shared VPC mode) ID of the transit gateway (can be found in the output of the main CloudFormation stack, in the TGWid key).
Additional Management Networks AWS 2nd Gen shell only Networks to be allowed to interact with all sandboxes. This is used for allowing connectivity to AWS resources outside the Management VPC.
The syntax is comma separated CIDRs. For example:
10.0.0.0/24,10.1.0.0/16,172.31.0.0/24.VPN Gateway ID AWS 2nd Gen shell only (Applies to Shared VPC mode only) ID of the gateway to use. Required to connect the shared VPC's sandbox subnets to the VPN gateway. CloudShell does this by creating a route between the specified VPN gateway and the connected subnet within the VPC CIDR. Can be found in the output of the shared VPC CloudFormation stack, in the VPNGWid key.
VPN CIDRs AWS 2nd Gen shell only (Mandatory for Shared VPC mode if VPN Gateway ID is defined) Comma-separated list of CIDRs in the local network to be used to VPN to the shared VPC. For example:
10.1.0.0/24,10.3.0.0/16Execution Server Selector All (Optional) This attribute points to a pre-defined group of execution servers (grouped by a common Execution Server Selector value). To make the association, enter the same value you specified on the execution server.
noteTo use the out-of-the-box Execution Server Selector attribute, make sure it has the "Execution Server Selector" rule. For details on how to add the rule to the attribute, see Defining attribute rules.
For additional information on managing App deployments per domains, see Managing Public Cloud Apps in Domains.
-
Click Start Discovery.
When the discovery process completes, a confirmation message is displayed. The cloud provider resource is displayed in the Inventory dashboard in CloudShell Portal and in Resource Manager Client.
To customize the App deployment types and publish App orchestration parameters, see Customizing App Deployment Types